Cybersecurity standards: what steps should you follow?

Benefit from effective IT support
Discover our all-in-one solution
ISO27001, SOC2, DORA... cybersecurity standards and labels have existed for several decades now, but still remain a mystery for many.
What are these standards that everyone is talking about? What do they mean? How do they differ?
We explain everything to you in this article.
The foundations of cybersecurity standards
What is a cybersecurity standard?
La cybersecurity is a dark world that seems almost impossible to tame.
So, in order to light the way and attest to the well-being of organizations rigorously following these rules essential to the security of digital environments and the protection of users, global and regional organizations have created labels, also called standards.
These cybersecurity standards are like a road map. They define best practices for secure your information systems, protect your data, and prevent risks.
In short: a standard is a guarantee that your organization follows a structured and reliable framework.
Standardization bodies
As mentioned, they are developed by specialized organizations, recognized internationally, to guide organizations in the face of growing threats.
Behind these standards, there are major players such as ISO (International Organization for Standardization) Or the International Electrotechnical Commission (IEC). They set internationally recognized standards.
Other organizations, such as the NIST (National Institute of Standards and Technology) in the United States, or regional initiatives such asANSSI in France, complete these frameworks to meet specific needs.
Each standard is the result of a consensus of experts: researchers, professionals, and decision-makers.
The goals of cybersecurity standards
Why follow a standard? The objectives are multiple:
• Integrity, Confidentiality, and Availability information.
• Reduction of cybersecurity risks.
• Compliance with current regulations, such as the RGPD or the directive NIS2.
• Strengthening of Stakeholder trust.
These objectives converge on a single goal: to ensure the resilience of your organization in an uncertain environment.
Detailed overview of the main cybersecurity standards
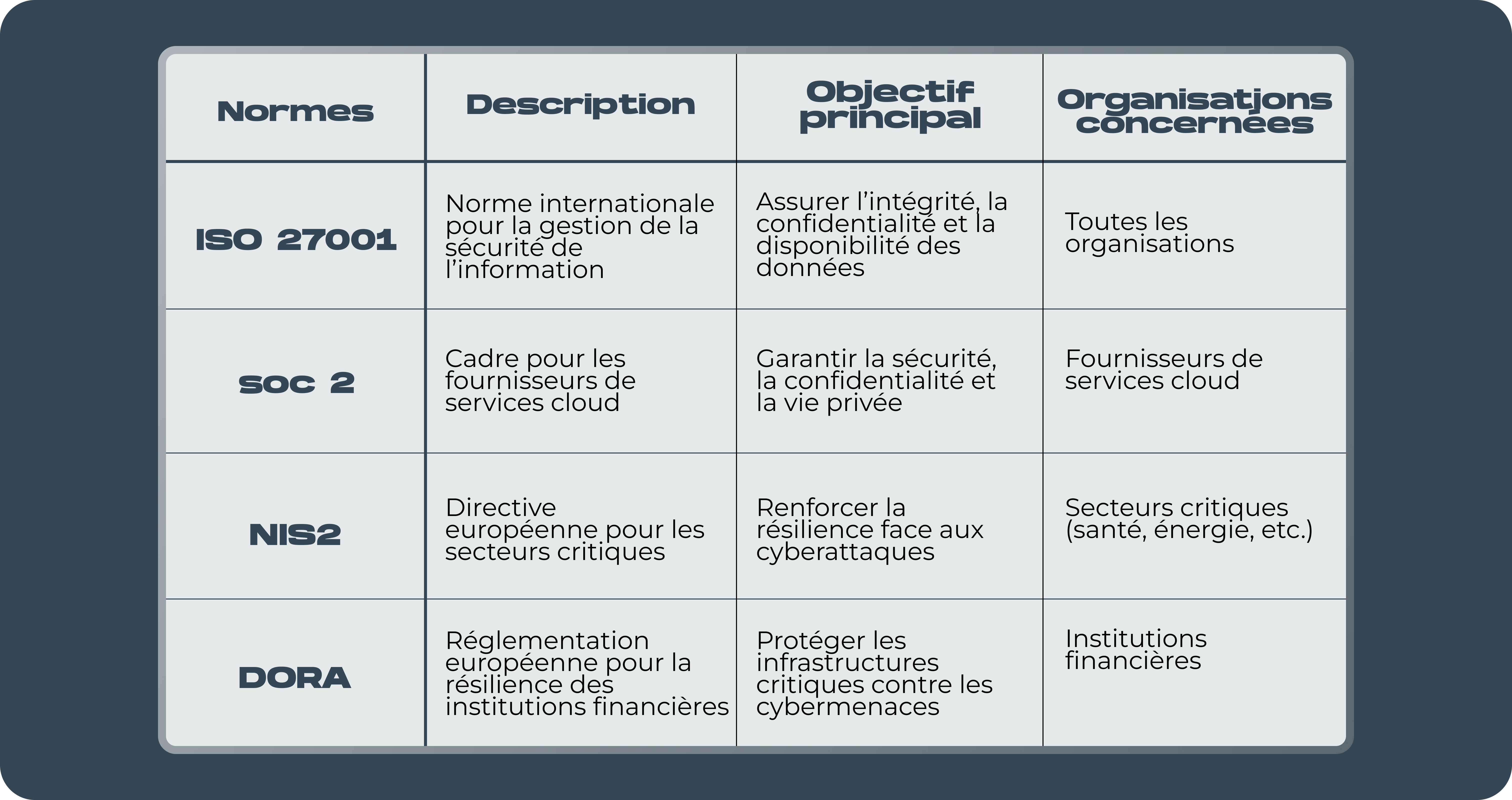
ISO 27001
THEISO 27001 remains the unavoidable standard when it comes to information security management. Recognized worldwide, it establishes the requirements for the implementation of a Information Security Management System (ISMS). The aim is to ensure the integrity, confidentiality, and availability of critical information for your organization.
ISO 27001 is based on an approach based on risk management, making it possible to identify and deal with threats specific to your environment. In addition, it adapts to organizations of all sizes and sectors, making it a universal solution.
👉 Discover our guide to ISO 27001.
Rzilient will support you to comply with this standard, as was the case with Boondmanager or MobilityWork.
SOC 2
Built for cloud service providers, SOC 2 is based on five trust criteria:
- security,
- Availability,
- Integrity of treatment,
- Confidentiality,
- Private life.
SOC 2 is particularly relevant for SaaS businesses or those that deal with large quantities of sensitive data for their customers. Certification proves that your organization follows rigorous processes to protect data, building stakeholder trust.
Nuances between SOC 2 Type I and Type II :
- Type I : Evaluate whether the controls are properly designed at a given point in time. Ideal for quick certification.
- Type II : Reviews the effectiveness of controls over an extended period of time (6 to 12 months), offering thorough and ongoing validation.
NIS2
The directive NIS2 (Network and Information Security Directive) is an evolution of the original NIS directive, adopted by the European Union. It targets critical sectors, such as telecommunications, health or energy, by imposing strict cybersecurity measures to prevent and respond to cyberattacks.
Among its main requirements:
• Implementation of robust risk management policies.
• Increased collaboration between Member States in case of incidents.
• Strengthening transparency and reporting obligations.
This directive is essential for any organization operating in the EU, and Rzilient offers personalized support to comply with it.
DORA
The regulations DORA (Digital Operational Resilience Act), also issued by the European Union, aims to strengthen the digital operational resilience of financial organizations. In an age of sophisticated cyberattacks, this regulation requires financial institutions to put robust measures in place to protect their critical infrastructures.
Requirements include:
• Of regular audits of cybersecurity.
• Strict management of risks associated with third party suppliers.
• One quick response and effective at incidents.
DORA is a major asset for companies looking to strengthen their cybersecurity posture in the financial sector.
Benefits of cybersecurity standards
Adopting a standard is much more than an administrative process. Here's what it can do for your organization:
1. Strengthened risk management
Cybersecurity standards help you anticipating and to manage risks before they become major problems. By following frameworks like ISO 27001 or SOC 2, you identify your vulnerabilities, assess their potential impact and put in place measures to limit them. This not only reduces the chances of a successful cyber attack, but also the costs associated with a data breach.
2. Increased trust in your customers and partners
Certified businesses demonstrate their commitment to safety. This reassures your customers, partners, and investors who know that their information is in good hands. It is a genuine competitive advantage, especially in sensitive sectors such as finance, health or e-commerce.
And not to mention!
Some standards, such as SOC 2, are often required by key account customers. Being certified can open the door to new business opportunities.
3. Simplified legal compliance
Between the RGPD, the guidelines NIS2 and sectoral regulations such as DORA, it's easy to feel overwhelmed. Cybersecurity standards allow you to check multiple boxes at once by integrating regulatory requirements into your strategy. This avoids costly sanctions and legal complications.
A concrete example? Compliance with NIS2, which requires risk management measures and regular audits, can be facilitated by adopting a standard like ISO 27001.
4. Improving operational efficiency
Standards don't just improve safety. They also promote better internal organization. By defining clear processes for incident management, employee training, or system maintenance, they save time and optimize resources.
Result: Your teams work with more serenity and less time lost due to unclear or ineffective procedures.
5. Increased resilience in the face of cyberattacks
Adopting cybersecurity standards means investing in the resilience of your organization. This means that even in the event of an incident, you have the tools, processes, and resources to respond quickly and limit the damage.
Important point: Resilience isn't just technical. Standards often include elements related to crisis communication, which are essential to protect your reputation in the event of a major incident.
6. A culture of safety within the organization
Certifications are not just a technical issue. They encourage collective awareness of cybersecurity issues, from interns to CEOs. This safety culture is becoming a strategic lever for mobilizing teams and empowering everyone in their practices.
Example: An employee who is trained in security will be more attentive to attempts to phishing or the use of unsecured devices.
Cybersecurity standards are evolving
The cyber threat landscape is constantly changing. Standards, too, are evolving to meet modern challenges: new types of attacks, data explosion, and the emergence of technologies such as AI.
As such, the standards now focus more on:
• The artificial intelligence risk management.
• The adoption of measures specific to teleworking.
• The global collaboration to deal with cross-border cyberattacks.
Rzilient can help you get certified in cybersecurity
Starting a certification process can seem daunting. Where do you start? What steps should you prioritize? Chez Rzilient, we're simplifying this process for you.
We support you every step of the way:
- Assessment of your existing system.
- Definition of the measures required to achieve compliance.
- Implementation and monitoring of best practices.
With our expertise, you are never alone on this journey to a safer digital environment.
Ready to take action? Contact us today and turn your challenges into opportunities!






