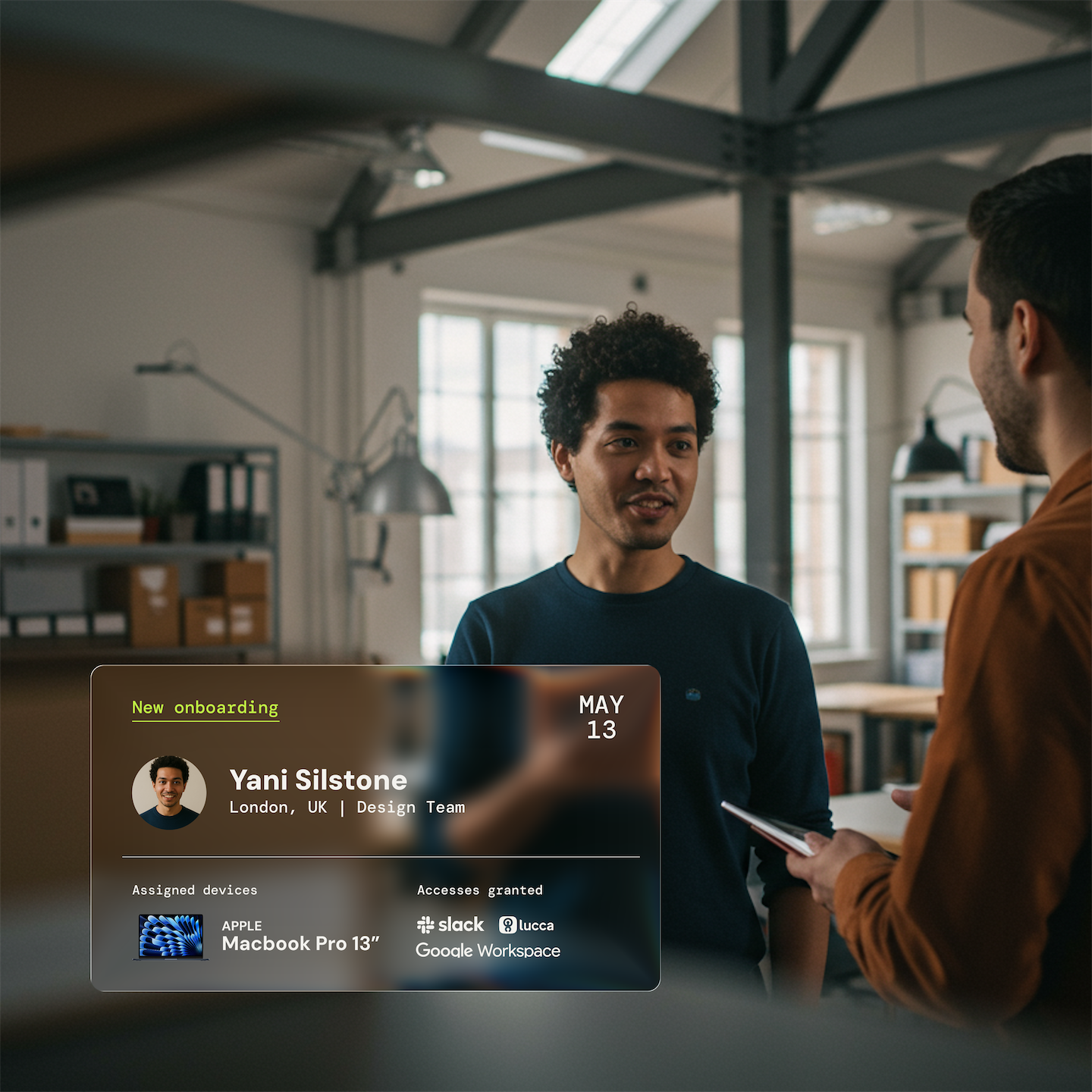
Centralized management of identities & authorizations
An identity and access management solution that saves your teams time, compatible with your SaaS, Hybrid or On-premise applications.
Identify key users
Identify and categorize the essential users of your system, giving them specific roles and permissions.
Ensure that each user has access to only the resources they need for their role, ensuring the security and confidentiality of sensitive data.
Securing data
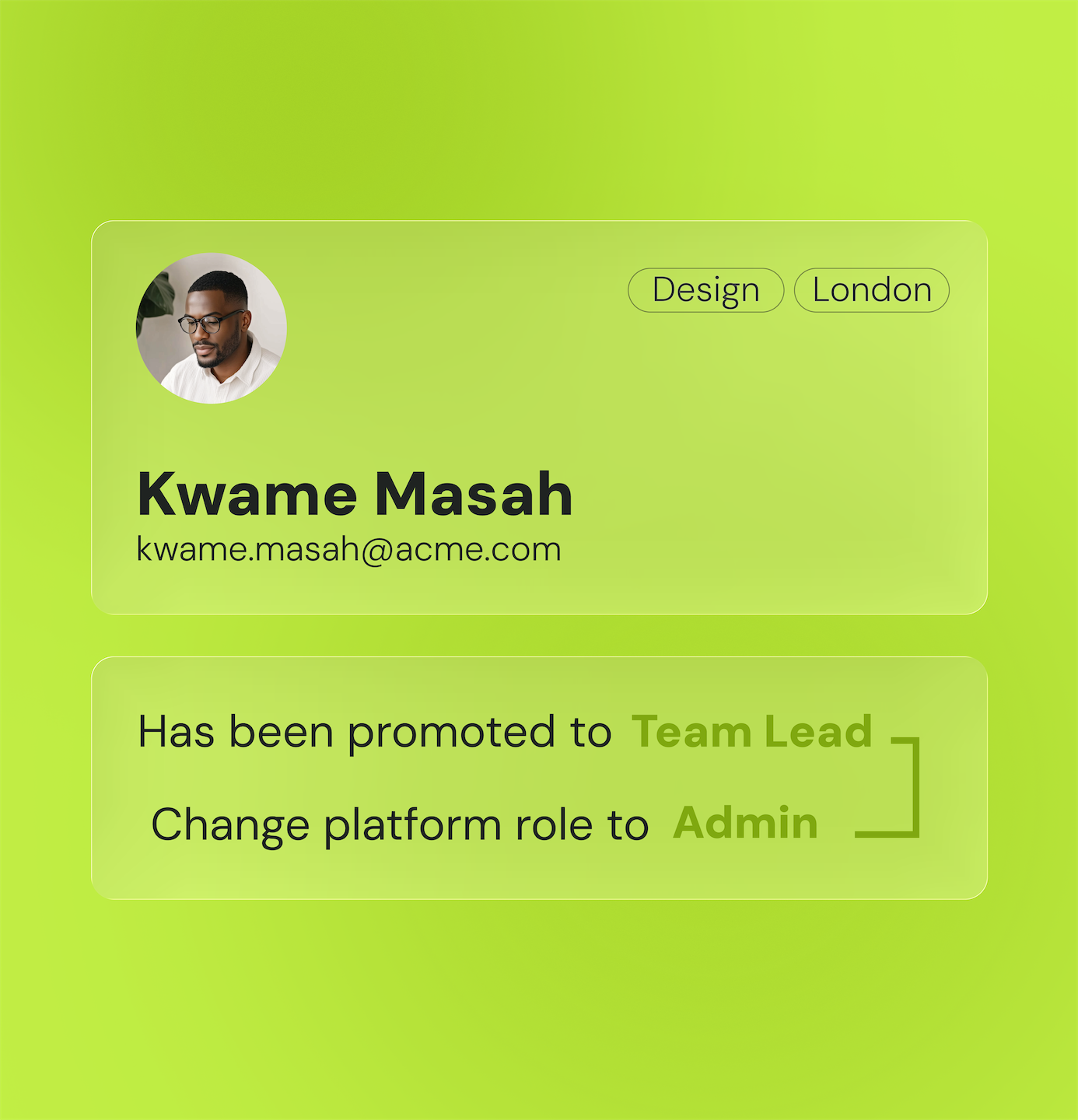
Simplify access management
Simplify access rights management by automating the processes for requesting, approving, and revoking permissions.
Reduce the risks of human error by implementing intelligent workflows and strict governance rules for every type of access.
Remote control
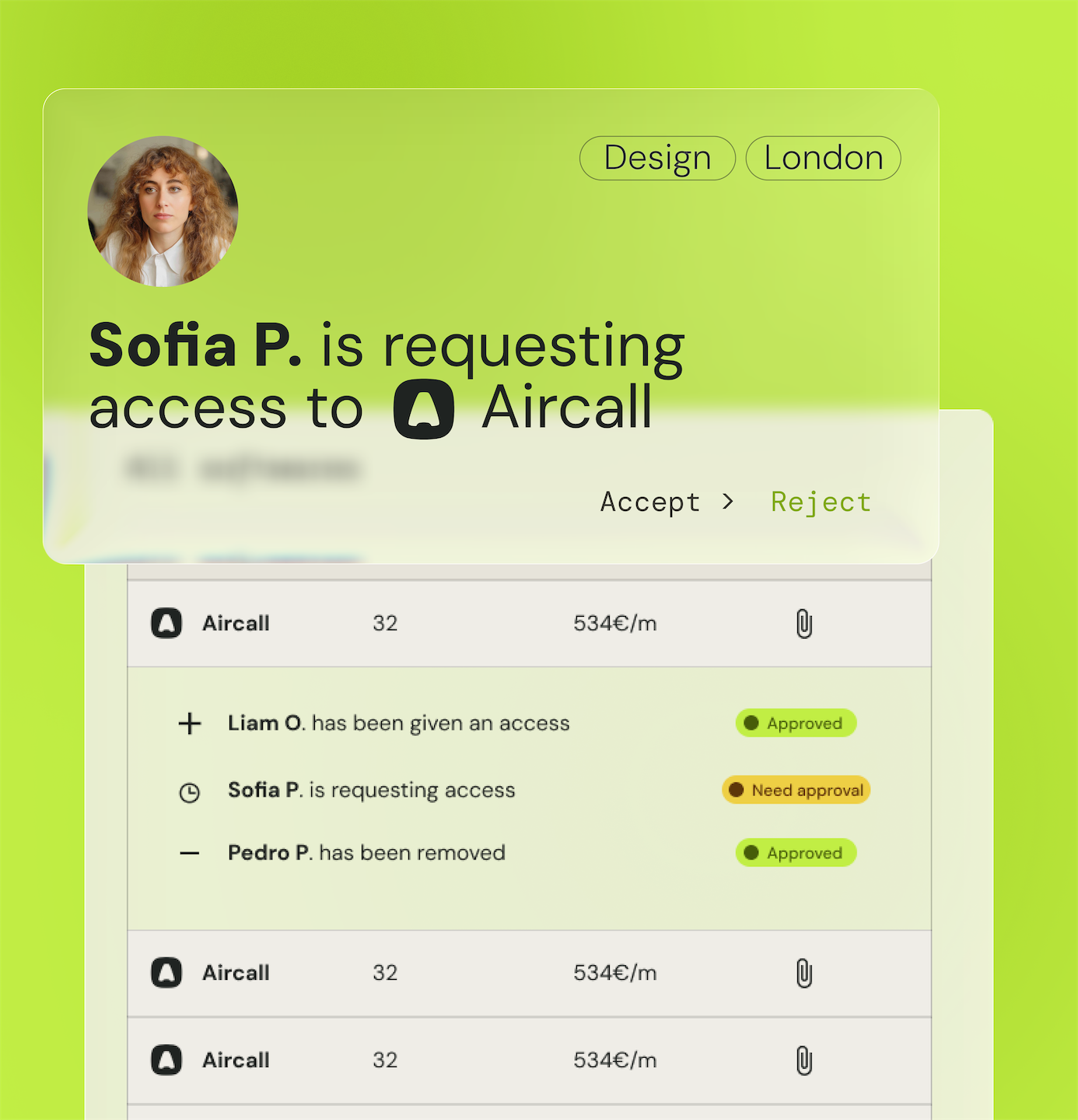
Strengthen data security
Protect sensitive information by implementing multi-factor authentication (MFA) mechanisms and robust encryption strategies.
Monitor user activities in real time to quickly detect and respond to suspicious behavior or unauthorized access attempts.
Proactive detection
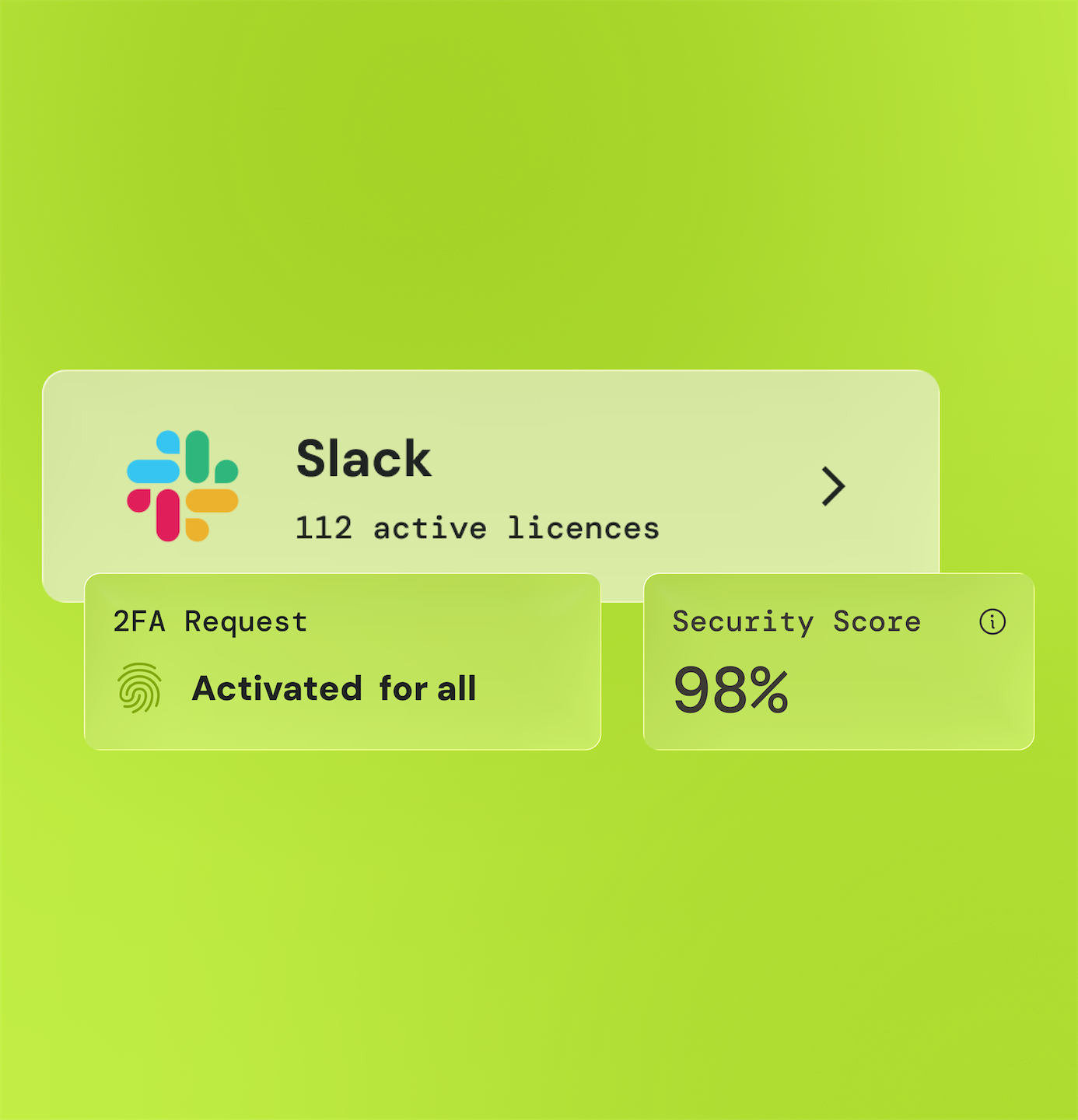
Ensure policy compliance
Stay in compliance with current regulations and security standards by automating reporting and auditing processes.
Ensure the traceability of user actions to meet compliance requirements and avoid potential fines and sanctions.
Compliance

Control your accesses securely
FAQs
Find our answers to your most frequently asked questions. Still having doubts? Talk to one of our experts!
We ensure that each user only has access to resources that are essential to their role, ensuring the security and confidentiality of sensitive data. This is achieved by carefully assigning roles and permissions that strictly correspond to the operational needs of the user.
Our solution automates the processes for requesting, approving, and revoking authorizations. This greatly simplifies access rights management while reducing human error and increasing operational efficiency.
All your IT equipment, in a single tool
Simplify your IT management with an intuitive SaaS platform and all the features you need.
MDM
Identities & Entitlements
On/Offboardings
Inventory
SaaS management