Understanding SSO and its challenges for your business

Secure your IT assets effortlessly
Discover our all-in-one solution
Tired of juggling 10 passwords a day, forgetting the HR app password, or reconnecting to HubSpot after every coffee break? Don't worry, you're not alone. It is precisely to respond to this digital fatigue that SSO (Single Sign-On) was created. In this article, we simply explain what it is, why it is useful for your IT and HR teams, and above all, how to set it up without getting lost in technical jargon.
What is SSO?
Definition of SSO
The Single Sign-On (SSO) is a method ofauthentication allowing a user to log in only once to access a set ofapps Or of web services. Instead of remembering several identifiers and passwords, the user enters their information only once via a identity provider Central who Manage accesses. This simplifies the lives of employees while strengthening the security computer science.
How does SSO authentication work?
SSO authentication is based on a dialogue between three actors:
- The user
- The identity provider (IdP)
- The service provider (SP)
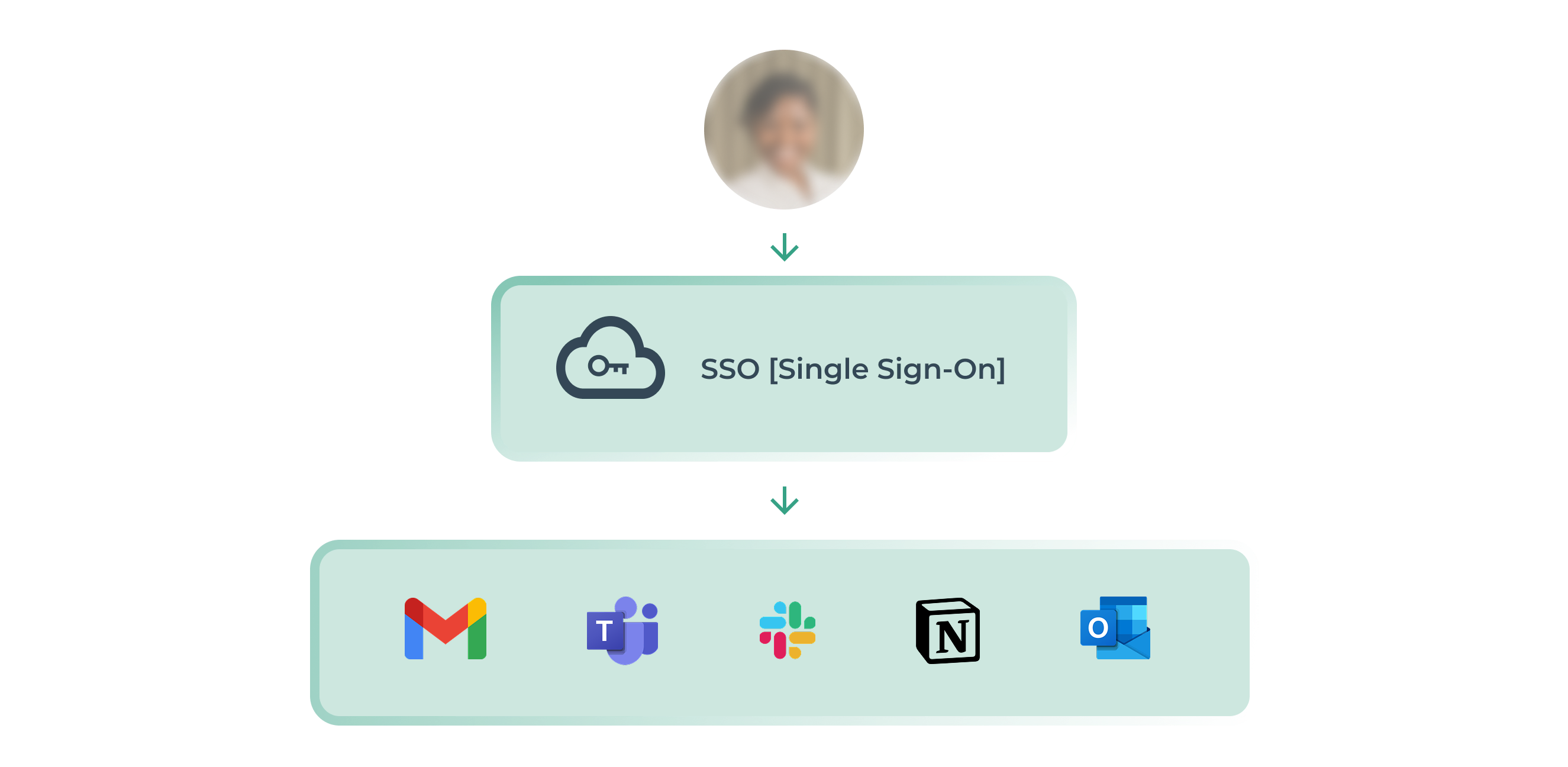
Concretely:
- You click on the URL of an application (HubSpot for example).
- You are redirected to your identity provider (like Google).
- You log in once.
- One authentication token is sent to verify your identity.
- You access other services without re-entering your login details
The benefits of integrating SSO into your business
The gains are concrete, both for technical teams and employees:
- Fewer passwords to remember, so fewer oversights and less friction.
- Fewer tickets for the IT support, often overwhelmed by reset requests.
- Enhanced employee experience, especially for onboarding.
- More security, with centralized authentication, easier to control.
- Fewer than Shadow IT : validated apps are more easily accessible.
In short, it's a small change that can transform the way your teams use their tools on a daily basis.
Implement SSO in your business
The different types of SSO
SAML (Security Assertion Markup Language)
The SSO veteran. Great for business apps like Google Workspace or Salesforce.
OAuth (Open Authorization)
Less to authenticate than to give partial access to data to another application. Typically used on APIs or to connect via a Google or Facebook account.
OpenID Connect (OIDC)
The modern and secure version of OAuth. Perfect for web and mobile apps
kerberos
A classic of Windows networking. Less used in cloud environments.
The criteria to take into account when choosing an SSO solution
Before getting started, a few questions to ask yourself:
- Are your tools (HubSpot, Notion, Slack...) compatible?
- What is your company's security policy?
- Do you want to maintain control over identity internally or do you want to go through a third party?
- Who will manage the connections? Your IT team, a service provider, or the Rzilient platform?
SSO integration and deployment
Here's what a successful SSO deployment looks like:
- Audit of your applications and needs : to identify priorities.
- Choosing an identity provider : Google, Azure AD, Okta...
- Setup : exchange of certificates, metadata, URLs...
- Tests : leave nothing to chance.
- Team training and support in case of problems.
With the Rzilient platform, we support you every step of the way to ensure a smooth integration without disrupting your business.

Comparing SSO with other access solutions
Federated identity management
The principle: you trust a third party to validate an identity (e.g. a B2B partner). We are in an inter-company logic.
Same sign-on
No single sign-in here. Just the same identifiers synchronized between multiple applications. Less practical, more rigid.
Multi-factor authentication (MFA)
The MFA add a step to your login: an SMS, a validation app, a fingerprint... It is often used In addition SSO for more security.
SSO is not a luxury: it is a real safety and efficiency reflex, especially for SMEs and scale-ups who manage more and more online tools. It is also a concrete way to improve the lives of your teams, while keeping control of what matters: accesses, data, identities.







